Master the Vulnerability Management Workflow for SMEs
- Gary Sinnott

- Dec 14, 2025
- 7 min read
Most British companies underestimate just how many digital and physical assets could put them at risk. With cyber threats targeting organisations of every size, building a complete picture of your business’s vulnerabilities has never been more crucial. Reports show that nearly half of British businesses encountered a cybersecurity breach in the past year alone. This guide walks through clear, practical steps to help you identify assets, automate security checks, and take action for stronger protection.
Table of Contents
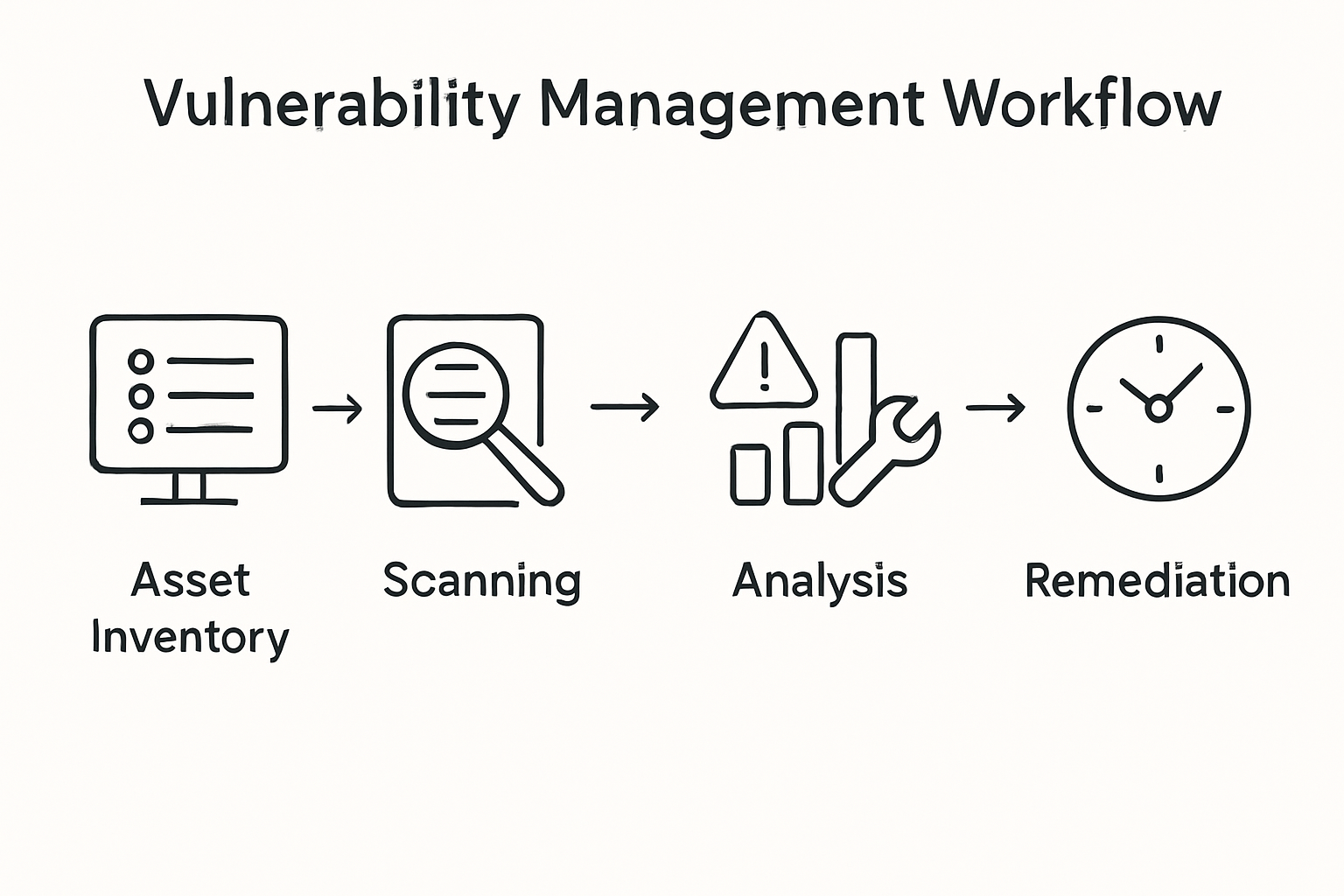
Quick Summary
Essential Insight | Detailed Explanation |
1. Create a Comprehensive Asset Inventory | Catalog all digital and physical assets to identify potential cyber risks within your organisation. Include less visible assets like mobile devices and databases. |
2. Implement Automated Vulnerability Scanning | Use tools that continuously monitor your technology ecosystem, advising on potential weaknesses. Schedule regular scans to ensure proactive security. |
3. Assess and Prioritise Vulnerabilities | Use a standardised risk assessment framework to categorise vulnerabilities by severity, focusing on critical threats that require immediate action. |
4. Develop a Structured Remediation Plan | Coordinate with technical teams to address discovered vulnerabilities, ensuring timely application of security patches tailored to impact severity. |
5. Establish Continuous Monitoring | Conduct regular scans post-remediation and set up a monitoring programme to detect new vulnerabilities swiftly, promoting an adaptive security posture. |
Step 1: Assess business assets and compliance scope
Identifying and mapping your business’s digital and physical assets forms the critical foundation of an effective vulnerability management workflow. This crucial first step involves systematically cataloguing every technology resource that could potentially expose your organisation to cyber risks.
Start by creating a comprehensive asset inventory that goes beyond obvious hardware. Include all computing devices, software applications, cloud services, network infrastructure, and digital information repositories. The UK Government Security Group emphasises understanding the value of information, applications, and infrastructure as a key strategy for evaluating potential cyber incident impacts. This means documenting not just your laptops and servers, but also less visible assets like employee mobile devices, third party software subscriptions, customer databases, and intellectual property digital archives.
To streamline this process, consider categorising assets by their criticality and potential vulnerability. The National Cyber Security Centre recommends identifying all assets including hardware, software, virtual infrastructure, information, and online accounts to effectively apply targeted security controls. Pro tip: involve team members from different departments to ensure no critical asset gets overlooked. An accounting system might seem mundane, but it could represent a significant risk if not properly secured.
Once you have a detailed asset inventory, map these against relevant compliance requirements specific to your industry. This prepares you for the next phase of vulnerability scanning and risk assessment.
Step 2: Set up automated vulnerability scanning tools
Automated vulnerability scanning tools transform your security strategy from reactive to proactive, systematically identifying potential weaknesses across your technology infrastructure. These powerful solutions continuously monitor your digital ecosystem, providing real time insights into potential security risks.
The National Cyber Security Centre recommends implementing regular automated scans for live services, which means selecting a tool that can thoroughly examine your entire network landscape. When choosing a scanning solution, prioritise tools that offer comprehensive coverage across different technology platforms including servers, cloud services, network devices, and endpoint systems. Look for features like continuous monitoring, detailed reporting, and the ability to integrate with your existing security infrastructure.
Implementing these tools requires strategic planning. The UK Ministry of Justice emphasises the importance of scanning during development and conducting ‘point in time’ scans following significant system changes. This means your vulnerability scanning approach should be dynamic rather than static. Consider scheduling regular scans that run automatically at predetermined intervals and configure alerts that notify your team immediately when critical vulnerabilities are detected. Pro tip: start with a baseline scan to understand your current security posture, then set up incremental scans that track changes and emerging risks over time.
With automated scanning tools in place, you are now ready to move towards interpreting and acting on the vulnerability data your systems generate.
Step 3: Review and prioritise identified vulnerabilities
After your automated scanning tools have completed their comprehensive sweep, you now face the critical task of understanding and prioritising the vulnerabilities discovered across your digital infrastructure. This process transforms raw scanning data into actionable security intelligence that protects your organisation.

The Ministry of Justice emphasises assessing vulnerabilities proportionally before progressing into production, which requires a systematic approach to vulnerability triage. Begin by categorising each identified vulnerability using a standardised risk assessment framework that considers factors like potential impact, exploitability, and potential damage to your business systems. Typically, vulnerabilities are ranked using a severity scale ranging from low to critical, with critical vulnerabilities demanding immediate attention and remediation.
The UK Government Security Group underscores the necessity of continuous vulnerability discovery to stay ahead of potential attacks, highlighting the importance of a proactive approach. Pro tip: develop a consistent scoring mechanism that weighs vulnerabilities not just by their technical severity, but by their potential business disruption. A seemingly minor vulnerability in a critical system might represent a more significant risk than a high severity issue in a peripheral network segment. Create a prioritised remediation roadmap that addresses the most dangerous vulnerabilities first while maintaining a comprehensive view of your overall security landscape.
With your vulnerabilities carefully assessed and prioritised, you are now prepared to develop a targeted remediation strategy that minimises your organisation’s security risks.
Step 4: Implement remediation actions and updates
Remediation represents the critical moment where your vulnerability management strategy transitions from identification to active protection. This stage requires precise execution and a systematic approach to addressing the security weaknesses discovered during your previous scanning and assessment processes.
The Ministry of Justice emphasises the importance of timely and strategic security patch application, highlighting that effective remediation goes beyond simply applying updates. Begin by creating a structured remediation plan that prioritises vulnerabilities based on their potential business impact. This involves coordinating with different technical teams to ensure each vulnerability receives appropriate attention and resources. Develop a clear protocol that defines response times for different severity levels critical vulnerabilities should be addressed immediately while lower risk issues can be scheduled more strategically.
The UK Government Security Group recommends providing comprehensive information to teams responsible for remediation and maintaining transparent reporting mechanisms. Pro tip: implement a tracking system that documents each vulnerability from initial discovery through complete resolution. This approach not only ensures thorough remediation but also provides valuable documentation for future audits and continuous improvement of your security posture. Regularly communicate progress to senior leadership to maintain organisational awareness and demonstrate the ongoing effectiveness of your vulnerability management programme.
With remediation actions completed, you are now prepared to validate the effectiveness of your security updates and continue your ongoing vulnerability management journey.
Step 5: Verify remediation and maintain continuous monitoring
Verification represents the crucial final stage of your vulnerability management workflow where you confirm the effectiveness of your remediation efforts and establish a robust ongoing monitoring strategy. This step transforms your security approach from reactive to proactively defensive.
The Ministry of Justice emphasises conducting regular automated vulnerability scans at specified intervals to ensure comprehensive security coverage. Begin by performing a comprehensive rescan of your entire digital infrastructure immediately after completing remediation actions. Compare the new scan results against your previous vulnerability assessment to confirm that all identified issues have been successfully addressed. Create a detailed verification report that documents each vulnerability status proving that your remediation efforts have effectively reduced potential security risks.
The Government Digital Service highlights the importance of proactive vulnerability detection before potential attackers can exploit system weaknesses. Pro tip: establish a continuous monitoring programme that includes automated scanning, periodic manual assessments, and real time alerting mechanisms. Configure your monitoring tools to provide immediate notifications for any new vulnerabilities or regression in your security posture. Develop a standardised process for reviewing and responding to these alerts that ensures swift action and minimal potential exposure.
With your verification complete and continuous monitoring established, you have now created a dynamic and responsive vulnerability management ecosystem that adapts and protects your organisation’s digital infrastructure.
Take Control of Vulnerability Management with Expert Support
Managing your assets, scanning for vulnerabilities, prioritising risks and implementing timely remediation can feel overwhelming for many SMEs. The article highlights the critical challenge of maintaining continuous visibility and control over your organisation’s evolving security landscape while meeting industry compliance demands. With pressures like limited time and resources, ensuring nothing gets missed is difficult but essential to prevent costly security breaches.
Freshcyber specialises in simplifying this complex journey through our tailored Vulnerability Management services, designed specifically for busy business owners and lean IT teams. Our Cyber Elite service automates key steps like scanning, prioritisation and remediation to keep your Cyber Essentials certification active and your defences strong all year round. We understand the stakes and ensure compliance does not become a last-minute scramble.

Discover how partnering with Freshcyber can remove the stress from your security programme and empower your team to focus on core business goals. Visit Freshcyber today to explore our expert-led options and take the first step towards mastering your vulnerability management workflow with confidence.
Frequently Asked Questions
What is the first step in the vulnerability management workflow for SMEs?
To start the vulnerability management workflow, you need to assess business assets and map your compliance scope. Create a comprehensive inventory of all digital and physical assets, including hardware, software, and information repositories, to identify potential cyber risks.
How can I set up automated vulnerability scanning tools effectively?
Implement automated vulnerability scanning tools by selecting a solution that covers your entire network landscape. Schedule regular scans to continuously monitor for potential weaknesses and establish alerts for immediate notifications when critical vulnerabilities are detected.
How do I prioritise vulnerabilities after scanning?
Prioritise vulnerabilities by categorising them based on their potential impact and exploitability. Use a standardised risk assessment framework to rank vulnerabilities and create a roadmap that focuses on addressing critical issues first while maintaining an overview of your security landscape.
What actions should I take for effective remediation of identified vulnerabilities?
For effective remediation, develop a structured plan that prioritises vulnerabilities based on their potential business impact. Coordinate with technical teams to address issues promptly, ensuring critical vulnerabilities are resolved immediately and track progress for future audits.
How can I verify the effectiveness of my remediation efforts?
Verify remediation efforts by conducting rescan assessments of your digital infrastructure after completing updates. Compare results with previous scans to confirm all identified vulnerabilities have been addressed, and document the status of each issue in a verification report.
What is the role of continuous monitoring in vulnerability management?
Continuous monitoring is essential in vulnerability management as it helps detect emerging vulnerabilities and potential regressions in your security posture. Establish a programme that includes regular automated scans and real-time alerts to ensure ongoing protection against threats.
Recommended
Comments