Security Patching: Strengthening SME Compliance Success
- Gary Sinnott

- 2 days ago
- 7 min read
Systems can quickly become vulnerable when critical updates are missed, leaving organisations exposed to threats that disrupt business and risk compliance. For IT Managers working in British SMEs, keeping pace with security patching is much more than box-ticking for Cyber Essentials. This guide offers practical steps and strategic insight into security patching as a proactive shield, helping you strengthen operational resilience and stay ready for audits.
Table of Contents
Key Takeaways
Point | Details |
Importance of Security Patching | Regular security patching is essential to protect against evolving cyber threats and mitigate vulnerabilities across organisational systems. |
Types of Patches | SMEs should focus on various patch types, including operating system, application, plugin, firmware, and driver updates, to maintain robust cybersecurity. |
Systematic Patching Process | A structured patch management process involving vulnerability identification, risk assessment, and timely deployment is crucial for effective security measures. |
Compliance and Documentation | Organisations must ensure compliance with standards like Cyber Essentials and maintain comprehensive patch management documentation to demonstrate vulnerability mitigation efforts. |
Defining Security Patching And Its Purpose
Security patching represents a critical defensive strategy for protecting digital infrastructure against evolving cyber threats. At its core, the process involves systematically updating software and systems to address known vulnerabilities and enhance overall security resilience.
The fundamental purpose of security patching is to mitigate potential security risks before malicious actors can exploit system weaknesses. By regularly applying vendor-released updates, organisations prevent potential breach points that could compromise confidential information, system functionality, and operational integrity.
Key components of effective security patching include:
Identifying software vulnerabilities across all system environments
Prioritising patches based on criticality and potential impact
Systematically testing and deploying updates
Maintaining comprehensive patch management documentation
Tracking and verifying successful patch implementation
From an operational perspective, security patching is not merely a technical task but a strategic risk management approach. Patch management involves comprehensive governance that requires coordinated efforts across IT infrastructure, security teams, and organisational leadership.
Security patches are the digital equivalent of closing doors before intruders can enter.
Vulnerability assessment forms the foundation of successful security patching. This process involves continuously monitoring software environments, identifying potential weaknesses, and proactively addressing them through timely, well-planned updates.
Pro tip: Develop an automated patch management workflow that prioritises critical security updates and minimises system downtime.
Types Of Security Patches Used In SMEs
Security patches play a critical role in protecting Small and Medium-sized Enterprises (SMEs) against rapidly evolving cyber threats. Different patch types address specific vulnerabilities across various technology environments, providing comprehensive defence mechanisms for digital infrastructure.
The primary categories of security patches used by SMEs include:
Operating System Patches: Updates addressing core system vulnerabilities
Application Patches: Fixes for software-specific security weaknesses
Plugin and Extension Patches: Updates for third-party software components
Firmware Patches: Updates targeting hardware-level security improvements
Driver Updates: Patches enhancing device communication and system stability
Each patch type serves a unique purpose in maintaining robust cybersecurity. Operating system patches are particularly crucial, as they address fundamental vulnerabilities that could potentially compromise entire network infrastructures. These updates protect against known exploits, close security gaps, and ensure system integrity.
Here’s how core patch types differ in their role and business impact:
Patch Category | Main Focus | Example Risks Mitigated | Business Impact |
Operating System | System-wide vulnerabilities | Network intrusions, exploit kits | Protects entire infrastructure |
Application | Software-specific flaws | Malware, ransomware infiltration | Secures business applications |
Plugin/Extension | Third-party components | Data theft, privilege escalation | Strengthens auxiliary systems |
Firmware/Driver | Hardware-level weaknesses | Device hijacking, stability loss | Safeguards device reliability |
Application patches represent another critical defence mechanism for SMEs. These updates target specific software vulnerabilities, preventing potential entry points for malware, ransomware, and other malicious activities. By systematically applying these patches, organisations can significantly reduce their exposure to cyber risks.

Firmware and driver updates are often overlooked but equally important. These patches address low-level system vulnerabilities that could provide attackers with direct access to hardware components, making them essential for comprehensive security strategies.
Pro tip: Implement a structured patch management process that categorises and prioritises updates based on their potential security impact and organisational risk profile.
How The Security Patching Process Works
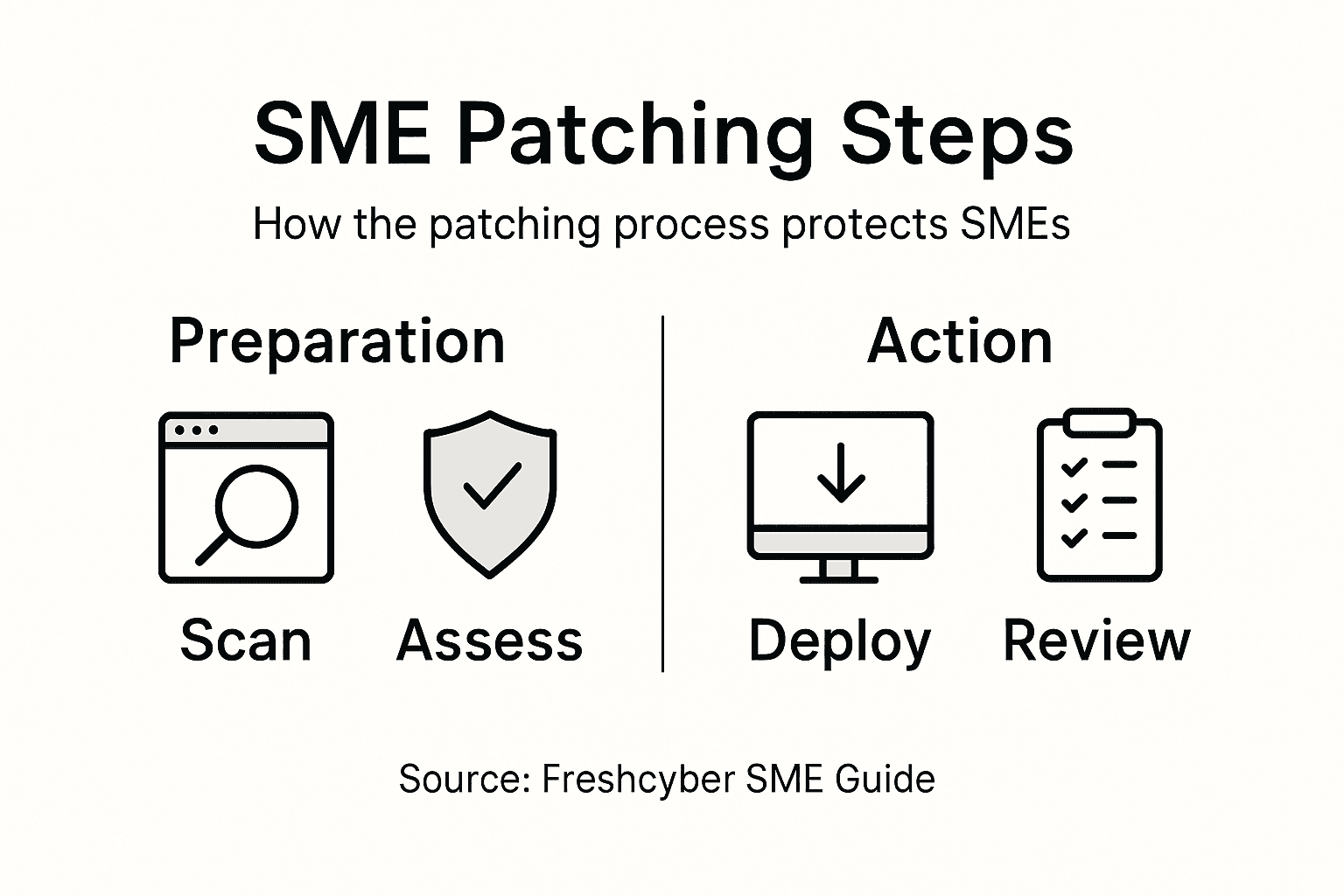
The security patching process is a systematic approach designed to protect organisational digital infrastructure from emerging cyber threats. Comprehensive vulnerability management involves a structured methodology that ensures timely and effective patch deployment across an organisation’s technological ecosystem.
Key stages of the security patching process include:
Vulnerability Identification: Scanning systems for potential security weaknesses
Risk Assessment: Evaluating the severity and potential impact of identified vulnerabilities
Patch Prioritisation: Ranking patches based on criticality and potential business disruption
Testing: Verifying patch compatibility and performance before widespread implementation
Deployment: Systematically applying patches across relevant systems
Verification: Confirming successful patch installation and system functionality
Vulnerability identification represents the crucial first step in the patching process. This stage involves using automated scanning tools and manual assessments to detect potential security gaps across all technological environments. Advanced asset management techniques help organisations maintain a comprehensive inventory of systems requiring attention.
Effective patch management is not about speed, but strategic and controlled implementation.
Risk assessment follows identification, where cybersecurity professionals classify vulnerabilities by potential impact. This process involves determining the potential damage a vulnerability could cause, considering factors such as system criticality, data sensitivity, and potential exploit complexity.
Patch deployment requires meticulous planning and execution. IT teams must carefully schedule updates to minimise operational disruption, often implementing patches during low-activity periods and maintaining robust backup systems to mitigate potential implementation risks.
Pro tip: Develop a documented patch management policy that establishes clear timelines, responsibilities, and escalation procedures for addressing security vulnerabilities.
Security Patching For Cyber Essentials Compliance
Cyber Essentials certification demands a rigorous approach to security patch management, requiring organisations to demonstrate systematic and proactive vulnerability mitigation strategies. This framework establishes clear guidelines for maintaining robust cybersecurity infrastructure through consistent and methodical patch deployment.
Key compliance requirements for security patching include:
Comprehensive Vulnerability Coverage: Addressing patches across all digital systems
Timely Update Implementation: Deploying patches within specified timeframes
Documented Patch Management Process: Maintaining transparent and auditable procedures
Regular System Scanning: Continuously identifying potential security weaknesses
Evidence of Patch Tracking: Providing detailed records of update applications
Patch management documentation plays a critical role in Cyber Essentials compliance. Organisations must create and maintain comprehensive records demonstrating their systematic approach to identifying, prioritising, and implementing security updates across their technological ecosystem.
Below is a summary of key Cyber Essentials patching requirements and what evidence is expected:
Compliance Aspect | Requirement Detail | Evidence Needed |
Vulnerability Coverage | Patches applied across all systems | Inventory records, asset logs |
Timely Implementation | Updates within specified timeframes | Patch timestamps, update logs |
Patch Management Process | Transparent, auditable documentation | Written procedures, process maps |
Regular System Scanning | Ongoing vulnerability identification | Scan reports, alert history |
Patch Tracking | Record all update activities | Audit trails, tracking systems |
Cyber Essentials certification is not just a checkbox, but a commitment to continuous security improvement.
The certification process requires organisations to provide concrete evidence of their patch management strategy. This involves presenting detailed logs, demonstrating consistent update protocols, and proving that vulnerabilities are addressed promptly and comprehensively.
IT teams must develop a structured approach that goes beyond simple patch application. This means creating a robust framework that includes vulnerability assessment, risk prioritisation, controlled deployment, and post-implementation verification.
Pro tip: Implement an automated patch management system that generates comprehensive audit trails and provides real-time reporting for Cyber Essentials compliance.
Risks Of Poor Patching And Audit Failures
Cybersecurity vulnerabilities can devastate Small and Medium-sized Enterprises (SMEs) when patch management is neglected. Cyber security breaches pose significant financial risks to organisations that fail to maintain rigorous update protocols.
Primary risks associated with poor patching include:
Financial Losses: Potential thousands of pounds in breach-related damages
Operational Disruption: Extended system downtime and productivity reduction
Regulatory Non-Compliance: Failing cybersecurity audit requirements
Reputational Damage: Loss of customer trust and potential business opportunities
Increased Vulnerability: Extended exposure to known security weaknesses
Unpatched systems create significant vulnerability windows that malicious actors can readily exploit. Each delayed update represents a potential entry point for cybercriminals seeking to compromise organisational networks, steal sensitive data, or install malicious software.
Neglecting patch management is equivalent to leaving your digital front door wide open.
Audit processes critically examine an organisation’s patch management governance, scrutinising the systematic approach to identifying, prioritising, and resolving security vulnerabilities. Failing to demonstrate a comprehensive and proactive patching strategy can result in immediate compliance failures.
The consequences extend beyond immediate financial impact. SMEs might face long-term repercussions including reduced market credibility, potential contract losses, and heightened insurance premiums resulting from perceived high-risk security practices.
Pro tip: Develop a documented patch management policy with clear escalation procedures and maintain comprehensive logs to demonstrate consistent vulnerability mitigation efforts.
Secure Your SME Compliance with Expert Patch Management
Security patching can be overwhelming, especially when your SME faces constant pressures to stay audit-ready and compliant. This article highlights the risks of poor patching and the need for meticulous vulnerability management to meet standards such as Cyber Essentials. If you want to move beyond just ticking boxes and instead build true digital resilience, it is crucial to adopt a strategic approach to security patching and ongoing risk mitigation.

Discover how Freshcyber transforms compliance into your strongest business asset through our tailored SME Security solutions. With our Compliance Currency Engine and vCISO-led leadership, we take full ownership of your patch management process delivering continuous vulnerability assessments, and fully auditable documentation. Don’t leave your security to chance when you can win bigger contracts and scale confidently. Visit Freshcyber today to secure your path to compliance success and operational peace of mind.
Frequently Asked Questions
What is security patching?
Security patching is the process of updating software and systems to address known vulnerabilities and enhance security resilience, helping to protect digital infrastructure from cyber threats.
Why is security patching important for SMEs?
Security patching is crucial for SMEs as it mitigates potential security risks by closing gaps that could be exploited by cybercriminals, ensuring the integrity of confidential information and operational systems.
How does the security patching process work?
The security patching process involves several stages: vulnerability identification, risk assessment, patch prioritisation, testing, deployment, and verification to ensure that updates are applied effectively across organisational systems.
What are the risks of poor patch management?
Poor patch management can lead to financial losses, operational disruption, regulatory non-compliance, reputational damage, and increased vulnerability to attacks, exposing organisations to significant risks and potential breaches.
Recommended
Comments