How to Prepare for Cyber Audit: Complete UK SME Guide
- Gary Sinnott

- Jan 3
- 8 min read

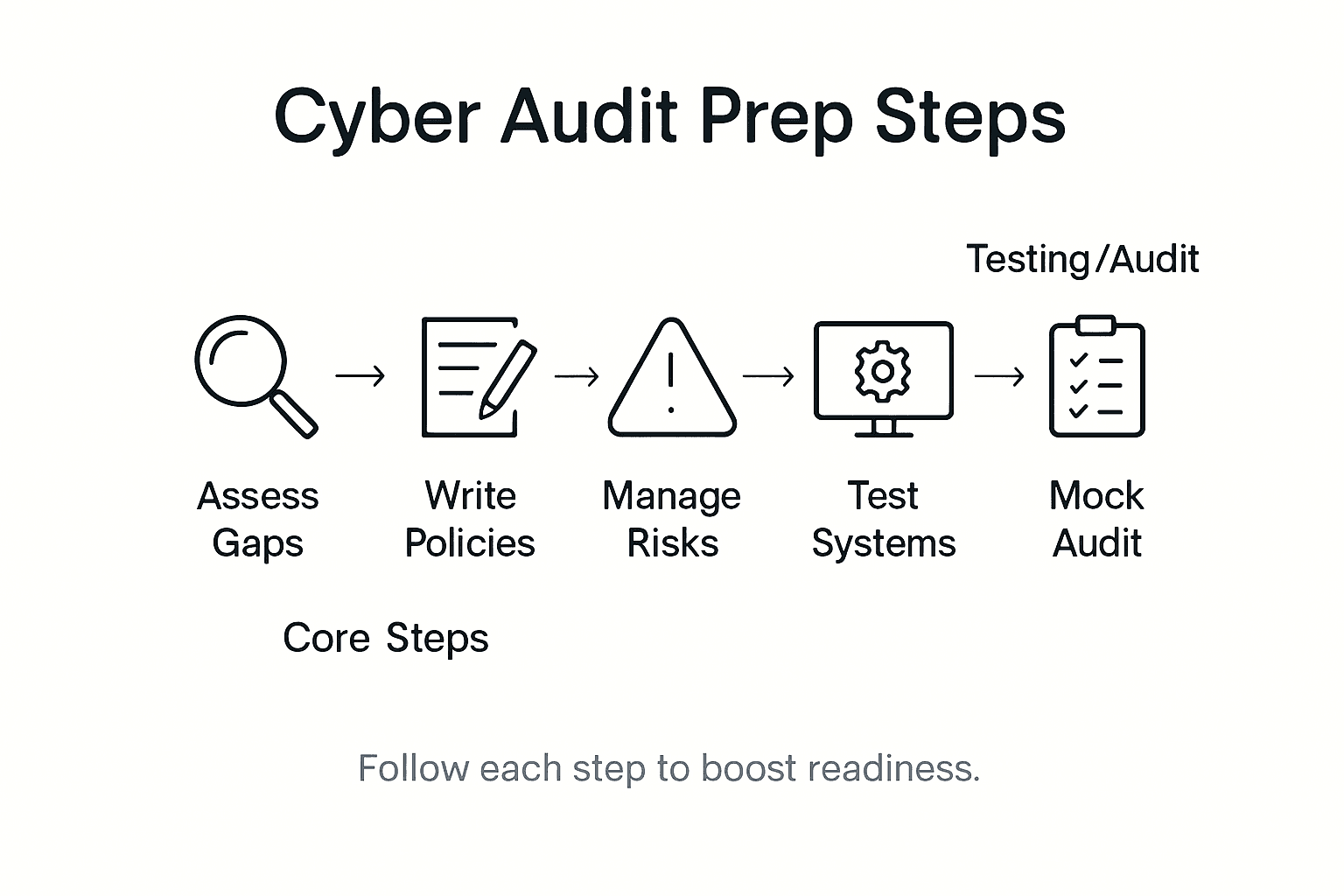
Nearly 60 percent of British legal and financial firms have faced client scrutiny over cyber audit readiness in the past year. For compliance officers and IT managers, a single overlooked vulnerability can jeopardise contracts or raise regulatory concerns. This guide lays out clear steps to help British organisations assess gaps, strengthen policies, and demonstrate robust data protection - giving your firm greater confidence ahead of any audit.
Table of Contents
Quick Summary
Key Point | Explanation |
1. Assess Current Security Posture | Conduct a thorough evaluation of your security landscape to identify vulnerabilities and areas needing improvement. |
2. Develop Comprehensive Security Policies | Document security policies that comply with regulations, outlining clear procedures for managing information security risks. |
3. Implement Multi-layered Protection Controls | Use both technical and human measures to safeguard your digital infrastructure and mitigate potential risks effectively. |
4. Conduct Regular Vulnerability Assessments | Employ automated scans and manual testing to discover hidden weaknesses and strengthen your organisation’s security. |
5. Perform Mock Assessments | Simulate real audit conditions to identify and rectify any remaining gaps, ensuring readiness for the official cyber audit. |
Step 1: Assess current security posture and identify gaps
Understanding your organisation’s current cybersecurity landscape is crucial before preparing for a cyber audit. This process involves conducting a comprehensive evaluation of your existing security controls, identifying potential vulnerabilities, and mapping out areas requiring improvement.
Begin by performing a thorough information security risk assessment that systematically examines your organisation’s security infrastructure. This involves cataloguing all digital assets, reviewing access controls, evaluating network configurations, and documenting potential entry points for cyber threats. Pay special attention to user permissions, data storage practices, and current security protocols. Your goal is to create a detailed snapshot of your current cybersecurity environment.
Next, map your existing security measures against recognised UK government frameworks like the NCSC Cyber Assessment Framework. Compare your current practices with recommended standards to pinpoint specific gaps in your security posture. Look for discrepancies in areas such as identity management, data protection, incident response capabilities, and supply chain security. Document these findings meticulously, as they will form the foundation of your improvement strategy.
Practical advice: Create a visual security gap matrix that colour codes vulnerabilities by severity level, helping your team quickly understand and prioritise remediation efforts.
Step 2: Develop and document key security policies
Documenting robust security policies forms the critical foundation for protecting your organisation’s digital assets and demonstrating compliance during cyber audits. These policies serve as comprehensive guidelines that outline your approach to managing information security risks, protecting sensitive data, and responding to potential cyber threats.
Start by developing comprehensive security policies that align with UK regulatory requirements. Your policy documentation should cover key areas such as data protection, user access management, incident response, remote working protocols, and third-party vendor security. Ensure each policy provides clear definitions of roles, responsibilities, and specific procedures. Consider addressing aspects like acceptable use of technology, password management, data classification, and communication security. These documents must be precise, actionable, and tailored to your organisation’s specific risk profile.
Each security policy should include implementation strategies, enforcement mechanisms, and regular review processes. Design policies that are both comprehensive and adaptable, allowing for periodic updates as technological landscapes and threat environments evolve. Engage key stakeholders across different departments to ensure the policies are practical and reflect the real operational needs of your organisation. Importantly, these policies should not just exist on paper but should be actively communicated, understood, and implemented across all levels of your business.
Practical advice: Create a central, easily accessible digital policy repository with version control, ensuring all employees can quickly reference the most up-to-date security guidelines.
Step 3: Implement risk management and protection controls
Implementing robust risk management and protection controls is a critical step in safeguarding your organisation’s digital infrastructure and preparing for a comprehensive cyber audit. This process involves systematically identifying potential vulnerabilities, assessing their potential impact, and developing targeted strategies to mitigate risks effectively.

Begin by conducting a structured risk assessment process.pdf) that methodically evaluates your organisation’s potential security weaknesses. This involves mapping out all digital assets, identifying potential threat vectors, and quantifying the potential business impact of each risk. Pay close attention to areas such as network access controls, data encryption, user authentication mechanisms, and third party vendor security. Prioritise risks based on their likelihood of occurrence and potential severity, creating a comprehensive risk register that allows for strategic resource allocation and targeted risk mitigation.
Implement multi layered protection controls that address both technical and human elements of cybersecurity. This includes deploying advanced endpoint protection systems, implementing robust access management protocols, conducting regular security awareness training, and establishing clear incident response procedures. Ensure that your protection controls are not static but dynamic and adaptable, with regular review and update mechanisms that allow your security posture to evolve alongside emerging technological landscapes and threat environments.
Practical advice: Develop a live risk dashboard that provides real time visibility into your organisation’s security status, enabling rapid identification and response to potential vulnerabilities.
Step 4: Conduct internal testing and vulnerability assessments
Conducting comprehensive internal testing and vulnerability assessments is a crucial step in identifying and addressing potential security weaknesses before they can be exploited by malicious actors. This proactive approach helps your organisation uncover hidden vulnerabilities and strengthen your overall cybersecurity resilience.
Begin by implementing a robust internal vulnerability assessment strategy that systematically scans your entire digital infrastructure. This process involves using automated scanning tools to identify potential security gaps across networks, systems, applications, and operational technologies. Focus on examining critical areas such as network configurations, user access controls, software patch levels, and potential entry points for cyber threats. Pay special attention to operational technologies that might have unique vulnerabilities, as these can often be overlooked in standard security assessments.
Complement your automated scanning with manual penetration testing techniques that simulate real world cyber attack scenarios. This involves employing skilled cybersecurity professionals who can identify and exploit potential vulnerabilities that automated tools might miss. The goal is not just to find weaknesses but to understand their potential business impact and develop targeted remediation strategies. Ensure you document all findings comprehensively, creating a detailed report that prioritises risks based on their potential severity and likelihood of exploitation. This approach demonstrates your organisation’s commitment to proactive security management and prepares you effectively for external cyber audits.
The table below contrasts manual and automated vulnerability assessments:
Aspect | Automated Scanning | Manual Testing |
Speed | Rapid identification of issues | Slower, thorough investigation |
Coverage | Wide system coverage | Targets complex vulnerabilities |
Cost | Lower ongoing cost | Higher due to human experts |
Depth | Surface-level findings | In-depth risk discovery |
Practical advice: Schedule vulnerability assessments quarterly and maintain a live tracking system that monitors the status of identified vulnerabilities from discovery to complete resolution.
Step 5: Verify audit readiness with mock assessments
Mock assessments are a critical final step in preparing for your official cyber audit, allowing you to simulate real audit conditions and identify any remaining gaps in your cybersecurity preparations. These rehearsal exercises provide an invaluable opportunity to test your organisation’s readiness and refine your security strategies before the actual audit.
Begin by developing a comprehensive mock assessment framework that closely mimics the conditions and scrutiny of an actual cyber audit. This involves creating scenarios that challenge your existing security controls, documentation practices, and incident response protocols. Engage independent cybersecurity professionals who can provide an objective external perspective and evaluate your systems as an auditor would. Focus on thoroughly examining your policy documentation, reviewing access management procedures, testing your incident response capabilities, and validating the effectiveness of your security controls.
During the mock assessment, treat the process as a genuine audit experience. Encourage your team to respond to simulated security challenges exactly as they would in a real audit scenario. Document all findings meticulously, paying close attention to any discovered weaknesses or inconsistencies. Use the insights gained to make final refinements to your security infrastructure, policies, and procedures. This approach ensures that when the actual audit occurs, your organisation will demonstrate a robust, well prepared, and professional approach to cybersecurity management.
Practical advice: Create a structured feedback mechanism that allows your team to learn from each mock assessment, turning potential vulnerabilities into opportunities for continuous improvement.
Here is a summary of each cyber audit preparation step and its key objective:
Step | Main Objective | Business Benefit |
Assess current security posture | Identify weaknesses and gaps | Gain clarity on vulnerabilities |
Develop security policies | Establish clear guidelines | Ensure consistent compliance |
Implement protection controls | Reduce risk exposure | Strengthen defence measures |
Conduct testing & assessments | Uncover hidden weaknesses | Enhance resilience to attacks |
Mock assessments | Simulate real audit conditions | Refine strategies before audit |
Elevate Your Cyber Audit Readiness with Expert Support from Freshcyber
Preparing for a cyber audit can feel overwhelming when faced with assessing your current security posture, developing comprehensive policies, or conducting thorough vulnerability assessments. This guide clearly outlines the key challenges UK SMEs face such as identifying security gaps, managing risks effectively, and ensuring audit readiness through mock assessments. If these steps seem complex or resource heavy, you are not alone.
Freshcyber acts as your trusted security partner, offering tailored solutions like our flagship Virtual CISO (vCISO) service to take ownership of your cyber strategy. We specialise in gap analysis, policy creation, risk management, and advanced testing techniques so your organisation is fully prepared for compliance with frameworks including Cyber Essentials and ISO 27001. Let us help you build true digital resilience and confidently face every audit with a strategic roadmap and continuous protection.
Start transforming your cyber readiness today by exploring our dedicated Compliance services, strengthening your defences with Vulnerability Management, and mastering the essentials through our Cyber Essentials expertise.

Take the critical step now to secure your SME’s future at Freshcyber and turn complex audit preparation into a clear, confident journey with expert guidance by your side.
Frequently Asked Questions
What is the first step in preparing for a cyber audit?
Assessing your current security posture is the first step in preparing for a cyber audit. Conduct a comprehensive evaluation of your existing security controls, identify vulnerabilities, and map out areas that require improvement within your organisation.
How can I identify vulnerabilities in my organisation’s cybersecurity?
Perform a thorough information security risk assessment to identify vulnerabilities in your organisation’s cybersecurity. Catalogue all digital assets, review access controls, and evaluate network configurations to understand where potential threats may exist.
What key areas should my security policies cover for a cyber audit?
Your security policies should cover several key areas including data protection, user access management, and incident response procedures. Ensure these policies are clear, actionable, and tailored to your organisation’s specific risk profile to demonstrate compliance effectively.
How often should I conduct internal testing and vulnerability assessments?
Conduct internal testing and vulnerability assessments at least quarterly to detect any potential security weaknesses. This frequency allows for timely identification and remediation of vulnerabilities, enhancing your overall cybersecurity resilience.
What is the purpose of a mock assessment before the cyber audit?
A mock assessment simulates real audit conditions to identify any remaining gaps in your cybersecurity preparations. Treat the mock assessment as a genuine audit scenario to refine your security strategies and ensure your organisation is fully prepared for the actual audit.
What should I document during the cyber audit preparation process?
Document all findings from your assessments, including identified vulnerabilities, policy changes, and testing results. Maintaining a detailed record will not only help in improving your security posture but also provide evidence of compliance during the actual audit.
Recommended
Comments