How to Pass Cyber Essentials Plus: A Complete UK Guide
- Gary Sinnott

- Dec 5, 2025
- 8 min read
Updated: Feb 8

Over half of British businesses have faced a cyber attack in the past year, highlighting just how critical strong digital defences have become. As threats grow more sophisticated, organisations across the United Kingdom are under pressure to meet strict security standards that protect sensitive data and maintain trust. Understanding each stage of the Cyber Essentials Plus journey helps you pinpoint weak points, take meaningful action, and stand out as a secure and responsible leader in the British business landscape.
Table of Contents
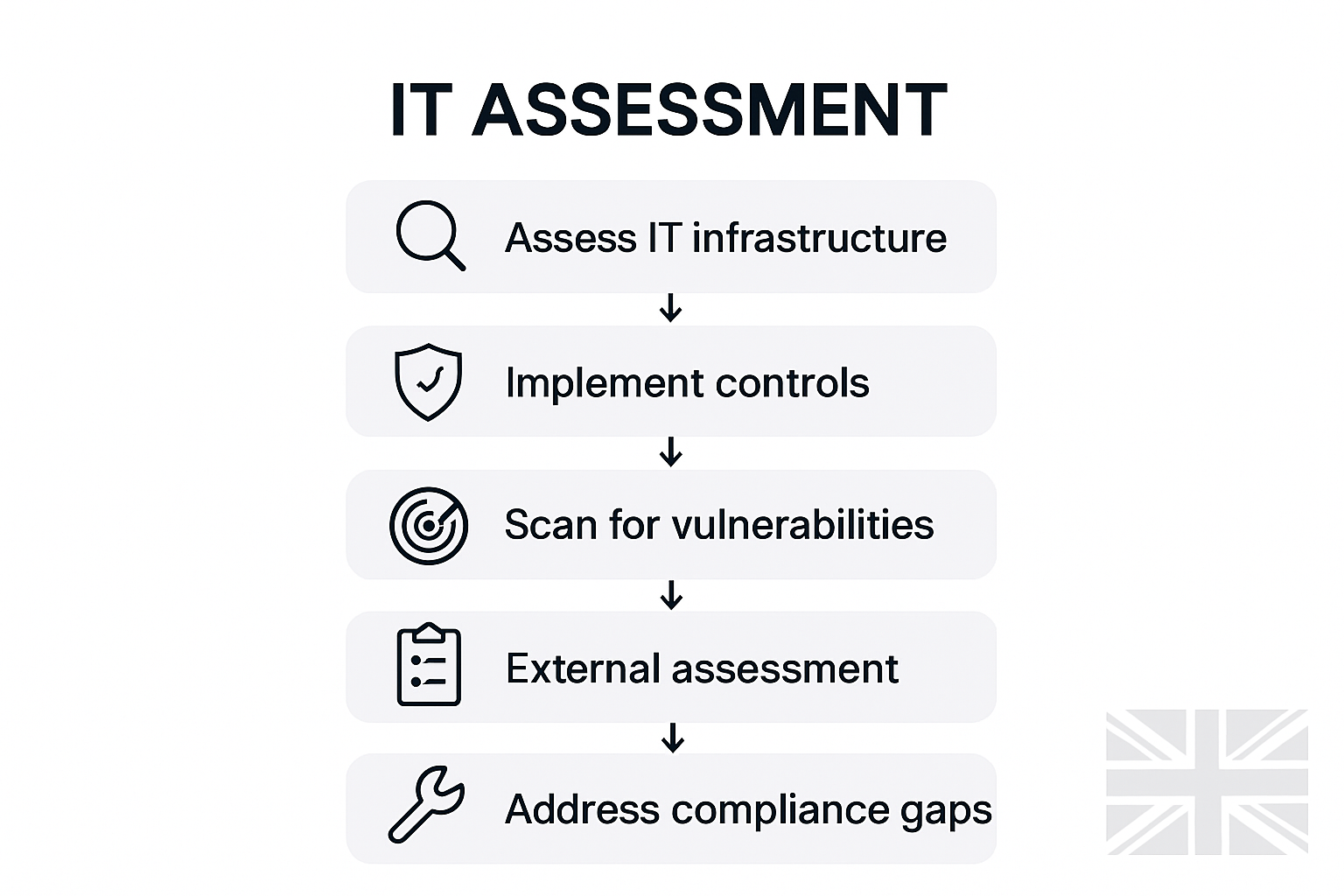
Stage 1: Assess Your Business Against Cyber Essentials Plus Requirements
Stage 2: Implement Essential Security Controls Across All Systems
Stage 3: Conduct Internal Vulnerability Scans And Remediate Issues
Stage 4: Engage An Accredited Assessor For External Certification Testing
Stage 5: Review Results And Address Any Remaining Compliance Gaps
Quick Summary
Summary Point | Explanation |
1. Assess Cyber Essentials Plus requirements | Conduct a detailed review of your IT infrastructure to identify vulnerabilities and align with Cyber Essentials standards. |
2. Implement essential security controls | Establish a security framework addressing firewalls, configurations, access control, malware protection, and updates to reduce cyber threats. |
3. Conduct internal vulnerability scans | Systematically identify and prioritise security weaknesses, patch systems, and adjust configurations to strengthen your cybersecurity posture. |
4. Engage an accredited assessor | An independent assessor validates your security measures through rigorous external testing to ensure compliance with Cyber Essentials Plus. |
5. Review and address compliance gaps | Analyse assessment results to prioritise and remediate vulnerabilities, viewing them as opportunities for continuous improvement in cybersecurity. |
Stage 1: Assess your business against Cyber Essentials Plus requirements
Assessing your business against Cyber Essentials Plus requirements is a strategic first step towards robust cyber security and demonstrating your organisational resilience. This comprehensive evaluation will help you identify potential vulnerabilities and understand how well your current systems align with the Cyber Essentials standards.
To conduct a thorough assessment, you will need to perform a detailed review of your organisation’s IT infrastructure, focusing on key technical controls specified by the National Cyber Security Centre. This involves examining your hardware and software configurations, network security protocols, and access management systems. Government guidelines recommend a systematic approach that covers endpoint security, firewall configurations, user access permissions, malware protection, and patch management.
A critical aspect of this assessment is understanding that Cyber Essentials Plus goes beyond basic self certification by requiring an independent technical verification. This means an external assessor will conduct hands-on testing of your systems, simulating real-world cyber attack scenarios to validate your security measures. Pay special attention to areas like remote access points, administrative privileges, and software update mechanisms, as these are often scrutinised during the technical assessment. Documenting your current security practices and being prepared to demonstrate their effectiveness will significantly improve your chances of successful certification.
Warning: Do not underestimate the complexity of this assessment. While it might seem daunting, breaking it down into systematic steps and seeking professional guidance can transform this from a challenging audit into a valuable opportunity to enhance your cyber resilience.
Stage 2: Implement essential security controls across all systems
Implementing essential security controls across all systems is a critical step in achieving Cyber Essentials Plus certification. This stage requires a comprehensive approach to securing your organisation’s digital infrastructure by addressing key technical vulnerabilities and establishing robust protective measures.
According to government guidelines, the implementation focuses on five fundamental technical controls: firewalls, secure configuration, user access control, malware protection, and security update management. Your goal is to create a holistic security framework that minimises potential entry points for cyber threats. Vulnerability management best practices recommend starting with a comprehensive audit of all systems, identifying potential weak points, and systematically addressing each area.
Each technical control requires specific strategies. For firewalls, ensure boundary protections are configured to filter incoming and outgoing network traffic. Secure configuration involves hardening system settings, removing unnecessary applications, and disabling default accounts. User access control demands implementing strong authentication mechanisms, using principle of least privilege, and maintaining detailed access logs. Malware protection requires deploying comprehensive endpoint security solutions with real-time scanning capabilities. Security update management means establishing a robust patch management process that ensures all systems receive timely updates and critical security fixes.
Warning: Implementing these controls is not a one-time task but an ongoing process. Cyber security requires continuous monitoring, regular assessments, and adaptive strategies to stay ahead of evolving digital threats.
Stage 3: Conduct internal vulnerability scans and remediate issues
Conducting internal vulnerability scans is a critical phase in achieving Cyber Essentials Plus certification, where you systematically identify and address potential security weaknesses across your organisation’s digital infrastructure. This process transforms your theoretical security strategy into a robust, actionable defence mechanism.
The National Cyber Security Centre test specification outlines detailed procedures for comprehensive vulnerability scanning, which involves using approved tools to comprehensively assess your network, systems, and endpoints. Vulnerability scanning techniques require a methodical approach that goes beyond surface level checks. This means conducting deep scans that simulate potential attack vectors, examining configuration settings, identifying unpatched software, detecting misconfigurations, and uncovering potential entry points for malicious actors.
Remediation is equally crucial and, under Cyber Essentials, strictly time-bound. After identifying vulnerabilities, you must prioritise them based on specific severity thresholds: any vulnerability with a CVSS v3 base score of 7 or above, or described by the vendor as 'critical' or 'high risk', must be remediated within 14 days of the fix being released. This involves patching systems, enabling automatic updates where possible, and ensuring all software remains licensed and supported - any unsupported software must be removed from the device or the scope entirely. Each vulnerability requires a targeted response, with these critical issues demanding immediate attention to meet the 14-day deadline, while lower-risk items should be scheduled for systematic resolution.
Warning: Vulnerability scanning is not a one time event but a continuous process. Cyber threats evolve rapidly, and what appears secure today might become a potential risk tomorrow.
Stage 4: Engage an accredited assessor for external certification testing
Engaging an accredited assessor marks the culmination of your Cyber Essentials Plus journey, transforming your internal security preparations into an officially recognised certification. This crucial stage involves an independent expert thoroughly validating your organisation’s security measures through rigorous external testing.
The National Cyber Security Centre test specification provides detailed guidelines for the external certification process, which involves comprehensive assessments across multiple dimensions of your digital infrastructure. Decoding the cyber audit process requires understanding that assessors will conduct both remote vulnerability scans and on-site technical evaluations. These assessments go far beyond automated checks, involving hands-on testing of your systems, simulating real-world attack scenarios, and examining the practical implementation of your security controls.
When selecting an assessor, prioritise those approved by recognised bodies such as IASME. The assessment will typically involve detailed technical testing of your endpoints, network infrastructure, and access management systems. Assessors will verify your internal vulnerability scan results, challenge your security configurations, and provide an objective evaluation of your cyber security posture. They will look for evidence of your implemented security controls, examining everything from patch management and software configurations to user access permissions and malware protection strategies.
Warning: The external assessment is not a box ticking exercise but a comprehensive examination of your organisation’s security readiness. Come prepared, be transparent, and view this as an opportunity to strengthen your cyber security infrastructure.
Stage 5: Review results and address any remaining compliance gaps
Reviewing the results of your Cyber Essentials Plus assessment is a critical phase that determines your final certification status. This stage transforms the detailed technical evaluation into actionable insights for strengthening your organisation’s cyber security posture.
The National Cyber Security Centre test specification provides comprehensive guidance on interpreting assessment findings. Common security vulnerabilities often emerge during this review process, requiring systematic and strategic remediation. Your assessor will provide a detailed report highlighting specific vulnerabilities, configuration weaknesses, and potential improvement areas across your digital infrastructure.
Addressing compliance gaps requires a methodical approach. Prioritise vulnerabilities based on their potential risk and potential impact on your organisation. Critical vulnerabilities demand immediate attention and rapid remediation, while lower risk items can be scheduled for systematic resolution. This might involve updating software patches, reconfiguring network settings, adjusting user access controls, enhancing endpoint security, or implementing additional protective measures recommended by the assessor.
Warning: Do not view compliance gaps as failures but as opportunities for continuous improvement. Each identified vulnerability is a chance to strengthen your cyber security defences and demonstrate your commitment to maintaining a robust security posture.
Take Control of Your Cyber Essentials Plus Certification Journey Today
Passing Cyber Essentials Plus requires rigorous preparation through assessing vulnerabilities, implementing critical security controls, and undergoing thorough external testing. Many UK SMEs struggle with juggling these complex tasks alongside daily business demands. Common challenges include managing continuous vulnerability scanning, maintaining compliance year-round, and avoiding last-minute surprises during audits.
At Freshcyber, we understand these pain points and provide expert guidance tailored for busy business owners and lean IT teams. Our comprehensive services ensure your organisation not only meets but maintains Cyber Essentials standards effortlessly. From our targeted support on essential security measures outlined in Cyber Essentials to seamless compliance management detailed in Compliance, we equip you with practical solutions for sustained cyber resilience.

Ensure your business stays ahead of evolving cyber threats with Freshcyber’s trusted consultancy. Visit our homepage now to learn more about how we can simplify your Cyber Essentials Plus certification and help you build lasting client trust. Take the first step towards stress-free, proven compliance today.
Frequently Asked Questions
What are the key steps to pass Cyber Essentials Plus certification?
To pass Cyber Essentials Plus certification, start by assessing your business against the Cyber Essentials requirements. Then, implement essential security controls, conduct internal vulnerability scans, engage an accredited assessor for external testing, and finally, review results to address any compliance gaps.
How can I identify vulnerabilities in my IT infrastructure?
You can identify vulnerabilities by conducting internal and external vulnerability scans using approved tools that assess your network and systems. Aim to perform these scans regularly, such as every quarter, to stay proactive about security weaknesses.
What are the five fundamental technical controls under Cyber Essentials Plus?
The five fundamental technical controls are firewalls, secure configuration, user access control, malware protection, and security update management. Implement these controls systematically across all systems to create a robust security framework.
How long does the Cyber Essentials Plus assessment process typically take?
The assessment process can take anywhere from a few weeks to a couple of months, depending on the size of your organisation and the complexities of your systems. Stay organised and prepared to facilitate quicker evaluations and corrections.
What should I do if I receive a report highlighting compliance gaps after my Cyber Essentials Plus assessment?
If you receive a report with compliance gaps, prioritise addressing vulnerabilities based on their potential risk and impact. Create a remediation plan to resolve critical issues swiftly, ideally within 14 days, while scheduling lower-risk items for systematic fixes.
Is it necessary to engage an external assessor for Cyber Essentials Plus certification?
Yes, engaging an external assessor is necessary as Cyber Essentials Plus requires independent verification of your security measures. Choose an accredited assessor to ensure a thorough review that will effectively validate your compliance with Cyber Essentials requirements.
Recommended
Comments