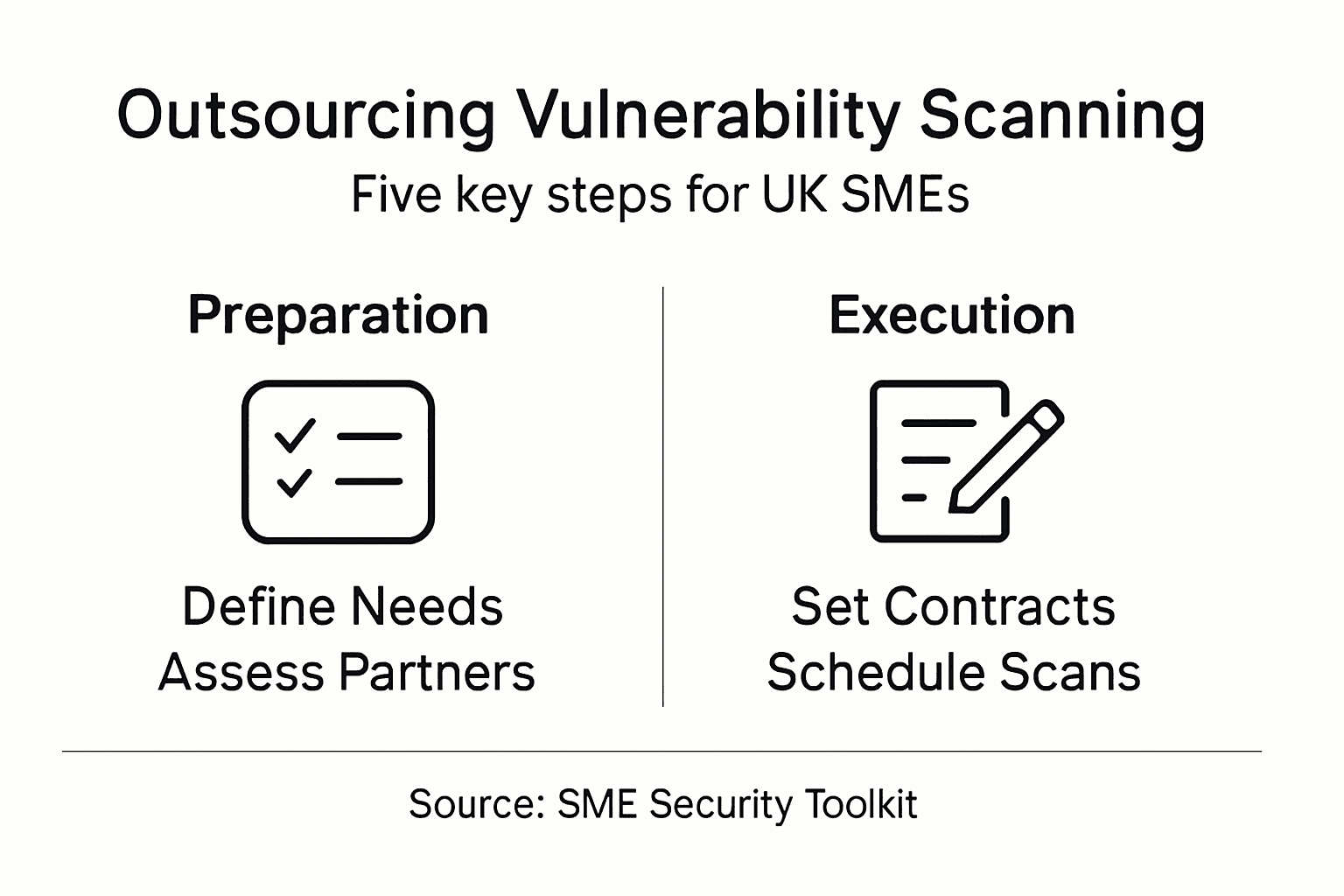
How to Outsource Vulnerability Scanning for UK SMEs
- Gary Sinnott

- 2 days ago
- 8 min read
Balancing daily demands with strict regulatory requirements leaves many British IT managers searching for efficient ways to keep their networks secure. For small and medium enterprises working towards ISO 27001 compliance, outsourcing vulnerability scanning is often the practical solution to resource pressures and complex threat environments. This guide breaks down the steps to define expert scanning requirements, select proven security partners, and implement contracts that uphold both robust cyber defence and legal compliance for your organisation.
Table of Contents
Quick Summary
Key Point | Explanation |
1. Define Scanning Requirements Clearly | Identify which systems, networks, and digital assets need to be scanned to ensure comprehensive security assessments. |
2. Choose the Right Cyber Security Partner | Evaluate potential vendors based on their technical expertise, industry experience, and client references to find the best fit for your needs. |
3. Establish Robust Contracts | Draft contracts that delineate data protection, remediation timelines, and compliance criteria to protect your organisation legally and operationally. |
4. Coordinate Scanning to Minimise Disruption | Plan scanning schedules around your operational rhythms, ensuring timely communication and minimal impact on business activities. |
5. Review and Verify Remediation Actions | Follow up on scan results to confirm vulnerabilities have been addressed effectively, ensuring thorough tracking and documentation for future assessments. |
Step 1: Define your vulnerability scanning requirements
Defining your vulnerability scanning requirements is the critical first step in creating a robust cyber defence strategy for your UK small or medium enterprise. This foundational process enables you to identify precisely what systems, networks, and digital assets need comprehensive security assessment.
To develop clear vulnerability scanning requirements, start by mapping out your entire digital infrastructure. This means cataloguing every network device, server, cloud service, and endpoint that connects to your organisation’s systems. Understanding comprehensive vulnerability assessment helps pinpoint exactly where potential security weaknesses might exist.
Consider these key aspects when defining your scanning requirements:
Comprehensive Coverage: Include all critical business systems and networks
Frequency of Scans: Determine how often different systems require assessment
Scanning Depth: Decide between surface-level or in-depth vulnerability probing
Compliance Requirements: Align scanning with industry-specific regulatory standards
The goal is creating a tailored vulnerability scanning approach that matches your specific business context and risk profile. Different organisations will need different levels of scanning intensity based on their digital complexity, industry regulations, and potential threat landscapes.
Here’s a comparative overview of scanning approaches in UK SMEs:
Approach Type | Typical Usage Scenario | Strengths | Limitations |
Surface-level scan | Basic infrastructure review | Quick risk identification | Misses deeper threats |
In-depth scan | Complex system scrutiny | Detailed vulnerability insight | Longer process, may disrupt ops |
Scheduled scan | Routine intervals | Consistency, compliance | May overlook urgent threats |
Ad-hoc scan | After major changes | Responsive to new risks | Less predictable, needs planning |
Effective vulnerability scanning isn’t about checking a box - it’s about understanding and mitigating your unique cyber risks.
Pro tip: Start with a pilot scanning programme on your most critical systems to understand your organisation’s specific vulnerability landscape before rolling out a full-scale assessment.
Step 2: Assess and shortlist reputable cyber security partners
Selecting the right cyber security partner is a critical decision that can significantly impact your organisation’s digital resilience. This step involves carefully evaluating potential vendors to ensure they can meet your specific vulnerability scanning and security management needs.
Begin by researching potential partners using comprehensive cyber security company evaluations. Look for providers with proven track records in supporting UK small and medium enterprises, focusing on key criteria that demonstrate their capabilities:
Technical Expertise: Assess their depth of technical knowledge and certifications
Industry Experience: Verify their experience in your specific business sector
Compliance Understanding: Confirm their familiarity with UK regulatory requirements
Service Breadth: Evaluate the range of security services they offer
Client References: Request and contact previous clients for genuine feedback
When shortlisting potential partners, create a detailed evaluation matrix that scores each vendor against your specific requirements. This systematic approach helps remove emotional or subjective decision-making and ensures you select a partner aligned with your organisation’s unique security needs.
Not all cyber security partners are created equal. Your goal is finding a partner who understands your specific business challenges.
Consider requesting detailed proposals from your top 3-5 shortlisted vendors. These proposals should provide clear insights into their methodology, scanning capabilities, reporting processes, and how they would approach your specific vulnerability management requirements.

Pro tip: Always schedule initial consultation calls with potential partners to assess their communication style, responsiveness, and cultural fit alongside their technical capabilities.
Step 3: Establish clear contracts and compliance criteria
Creating robust contracts and compliance frameworks is crucial when outsourcing vulnerability scanning for your UK small or medium enterprise. This step ensures that your chosen cyber security partner understands and meets your specific legal, regulatory, and security requirements.
When drafting contracts, focus on comprehensive regulatory compliance criteria that protect your organisation’s interests. Your contract should explicitly outline critical elements that demonstrate accountability and shared security responsibilities:
Data Protection Clauses: Specify GDPR compliance requirements
Security Control Definitions: Detail expected security measures
Remediation Timelines: Set clear expectations for addressing identified vulnerabilities
Reporting Mechanisms: Define frequency and depth of vulnerability reporting
Audit Rights: Include provisions for independent security assessments
Ensure your contract addresses key compliance dimensions beyond technical specifications. This means defining data ownership, encryption standards, access control protocols, and incident response procedures that align with UK regulatory frameworks.
Below is a summary of essential contract clauses for outsourced scanning partnerships:
Clause Category | Business Impact | Why It Matters |
Data Protection (GDPR) | Shields client data | Mandatory for UK legal compliance |
Remediation Timelines | Accelerates threat response | Reduces exposure duration |
Audit Rights | Enables independent review | Verifies partner accountability |
Documentation Standards | Facilitates reporting and review | Improves clarity and ongoing compliance |
A well-crafted contract is your primary defence against potential security and legal risks in vulnerability scanning partnerships.
Consider engaging a legal professional with cyber security expertise to review the contract. They can help identify potential gaps and ensure your agreement provides comprehensive protection for your organisation’s digital assets.
Pro tip: Request sample incident response documentation from potential partners to verify their practical approach to managing and communicating security vulnerabilities.
Step 4: Coordinate scan scheduling and secure data transfer
Effective coordination of vulnerability scanning requires meticulous planning to minimise disruption to your business operations while maintaining robust security protocols. This step focuses on establishing seamless communication and scheduling mechanisms with your chosen cyber security partner.
When planning your scanning schedule, follow strategic vulnerability scanning guidance to ensure minimal operational impact. Develop a comprehensive scanning strategy that considers your organisation’s unique operational rhythms:
Timing Windows: Identify least disruptive scanning periods
System Criticality: Prioritise scans for mission-critical infrastructure
Notification Protocols: Establish clear communication channels
Frequency Parameters: Define regular and ad-hoc scanning intervals
Change Management: Schedule additional scans after significant system updates
Secure data transfer is equally critical. Implement robust encryption and access control mechanisms to protect sensitive information during the vulnerability assessment process. This means using secure communication channels, establishing strict data handling protocols, and ensuring all transferred information remains confidential.
Successful vulnerability scanning is a dance of precision: minimising disruption while maximising security insights.
Encourage transparent communication between your team and the scanning partner. Regular check-ins and clearly defined escalation procedures will help manage expectations and quickly address any potential issues that arise during the scanning process.
Pro tip: Create a dedicated communication channel and assign specific team members to manage scanning coordination and data transfer to streamline the entire process.
Step 5: Review scan results and verify remediation actions
Reviewing vulnerability scan results and confirming that remediation actions have been effectively implemented is a critical final stage in your outsourced scanning process. This step ensures that identified security weaknesses are not just reported, but actually resolved.
Utilise systematic remediation tracking tools to comprehensively assess the progress of vulnerability resolution. Your approach should be methodical and thorough, focusing on verifying each identified issue:
Detailed Comparison: Cross-reference original scan findings with remediation reports
Risk Prioritisation: Confirm high-risk vulnerabilities received immediate attention
Evidence Validation: Request concrete proof of implemented security fixes
Technical Verification: Conduct follow-up technical assessments
Documentation Review: Examine comprehensive remediation documentation
Effective verification requires a collaborative approach with your cyber security partner. Request detailed reports that not only highlight resolved vulnerabilities but also provide insights into the specific actions taken, tools used, and methodologies employed during the remediation process.
Not all vulnerabilities are created equal: focus on understanding the depth and quality of remediation, not just the quantity of issues addressed.
Establish a clear feedback loop with your security partner, ensuring ongoing communication about any emerging or persistent vulnerabilities. This continuous dialogue helps maintain a proactive security posture and demonstrates a commitment to robust cyber defence.
Pro tip: Develop a standardised remediation verification checklist that can be consistently applied across different scanning cycles to ensure comprehensive and uniform security assessment.
Strengthen Your SME’s Cyber Defence with Expert Vulnerability Management
Outsourcing vulnerability scanning is just the first step in building a resilient security posture for your UK SME. If you want to move beyond basic scans and towards a strategic, comprehensive approach that includes identifying, prioritising, and remediating risks, Freshcyber is here to help. We understand the challenge of balancing thorough vulnerability analysis with minimal operational disruption and compliance demands.
Our Vulnerability Management solutions provide the expertise and leadership your business needs. From in-depth internal and external scanning to ongoing risk assessment, our Virtual CISO service acts as the “brains” of your security strategy. We work closely with you to create actionable plans aligned with industry standards and compliance frameworks covered in our Compliance portfolio. With Freshcyber as your dedicated security partner, your SME can confidently tackle cyber threats with proven strategic support.

Take control of your digital resilience today. Discover how our tailored security services can help your SME stay secure and compliant by visiting Freshcyber. Let us guide you every step of the way towards a safer future.
Frequently Asked Questions
How do I define my vulnerability scanning requirements for outsourcing?
To define your vulnerability scanning requirements, start by cataloguing all your digital assets such as network devices and cloud services. Assess aspects like coverage, scanning frequency, and compliance to create a tailored plan that suits your business context.
What should I look for when assessing potential cyber security partners?
When assessing potential cyber security partners, focus on their technical expertise, industry experience, and understanding of compliance standards. Create an evaluation matrix to compare vendors against your specific requirements to ensure a good fit for your organisation’s needs.
How can I establish clear contracts with my cyber security partner?
Establish clear contracts by outlining data protection clauses, security control definitions, and remediation timelines. Ensure that the agreement covers compliance criteria and accountability measures to protect your organisation’s interests during the scanning process.
What steps should I take to coordinate scan scheduling with my partner?
To coordinate scan scheduling, identify least disruptive periods for scanning and establish clear communication protocols with your partner. Develop a comprehensive strategy that includes time windows and notification procedures to facilitate a smooth process.
How can I effectively review scan results and verify remediation actions?
To review scan results, cross-reference original findings with remediation reports and request evidence of fixes from your cyber security partner. Conduct follow-up assessments to ensure that high-risk vulnerabilities have been addressed and document the results thoroughly.
Recommended
Comments