Complete Guide to Passing Cyber Essentials Audit UK
- Gary Sinnott

- Dec 7, 2025
- 7 min read

Over 80 percent of small and medium British businesses are at risk of cyber attacks due to gaps in their basic security controls. With regulations and threats evolving rapidly across the United Kingdom, understanding how to achieve Cyber Essentials certification is more crucial than ever. This guide breaks down every critical step, revealing practical strategies to help you meet official standards and protect your organisation from costly breaches.
Table of Contents
Quick Summary
Key Point | Explanation |
1. Understand Cyber Essentials requirements | Familiarise yourself with the core security standards set by the NCSC to protect your infrastructure from cyber threats. |
2. Document existing security controls | Compile a detailed evidence portfolio showcasing your organisation’s adherence to Cyber Essentials technical controls. |
3. Implement necessary security improvements | Focus on enhancing firewall, configuration, user access, malware protection, and patch management measures across your organisation. |
4. Conduct internal vulnerability scans | Regularly perform scans to identify and address potential security weaknesses before the official audit. |
5. Prepare thorough self-assessment submission | Submit a comprehensive workbook containing well-organised and relevant evidence of your cyber security practices. |
Stage 1: Understand the Cyber Essentials audit requirements
Passing the Cyber Essentials audit begins with comprehending the core security standards that the UK National Cyber Security Centre (NCSC) has established for organisations. Your primary goal is to demonstrate a baseline level of cyber security protection that safeguards your digital infrastructure against common online threats.
The Cyber Essentials certification requires businesses to meet specific technical controls across five key areas: firewalls, secure configuration, user access control, malware protection, and security update management. These requirements are designed to ensure your organisation implements fundamental security practices that prevent the most common cyber attacks.
When preparing for the audit, you will need to complete a comprehensive self-assessment questionnaire that thoroughly examines your current security infrastructure. This may involve providing detailed evidence of how your systems meet each mandatory control, potentially including network configuration screenshots, security policy documentation, and proof of ongoing vulnerability management.
A critical tip for success is meticulous documentation. Assessors will scrutinise every detail, so ensure you maintain clear, organised records of your security configurations and demonstrate a proactive approach to cyber defence. By understanding these requirements early, you can methodically prepare and increase your chances of achieving certification smoothly.
Stage 2: Assess and document your current security controls
The critical next step in achieving Cyber Essentials certification involves meticulously assessing your organisation’s existing security infrastructure. This comprehensive evaluation requires a systematic approach to documenting and validating your current cyber security practices across multiple operational domains.
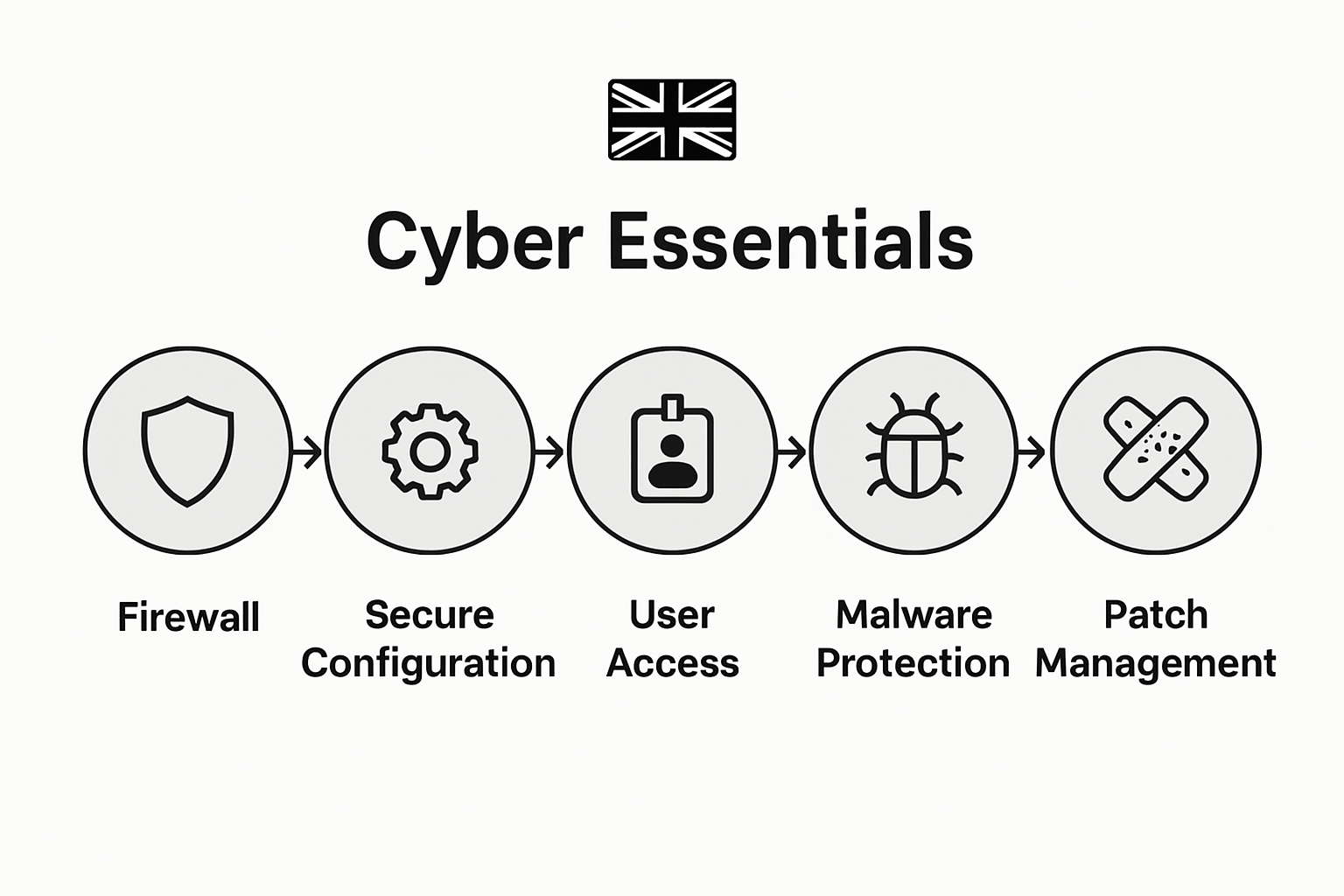
To effectively prepare for the audit, you must compile detailed information that demonstrates your organisation’s adherence to key security controls. This process involves gathering technical details such as network configuration settings, user access lists, security update management records, and firewall rules. Your internal documentation should provide the necessary detail to confirm your systems implement protective measures against potential cyber threats. Pay particular attention to verifying system policies and settings so that you can provide accurate answers and evidence if requested by the Certification Body.
A strategic tip for success is to approach this preparation with precision and clarity. Assessors will scrutinise your answers, so ensure your information is well organised, current, and directly addresses each of the Cyber Essentials requirements. By creating a comprehensive and transparent record of your security controls, you significantly increase your chances of passing the certification audit and demonstrating your commitment to robust cyber defence practices.
Stage 3: Implement necessary improvements and controls
Implementing security improvements is a critical phase in achieving Cyber Essentials certification. Working with certified Cyber Advisors can provide structured guidance on addressing any identified vulnerabilities and strengthening your organisation’s security infrastructure.
Your implementation strategy should prioritise addressing the five key control areas: firewalls, secure configuration, user access management, malware protection, and patch management. This involves developing and executing a comprehensive action plan that systematically resolves identified security gaps. Each improvement should be carefully documented, with clear evidence of implementation such as updated system configurations, revised security policies, and proof of technical modifications. Pay close attention to creating robust access control mechanisms, ensuring all user accounts have appropriate permissions and implementing multi factor authentication where possible.

A strategic approach is to treat this process as an ongoing journey rather than a one time fix. Continuous monitoring and incremental improvements will not only help you pass the Cyber Essentials audit but also build a resilient security posture that adapts to evolving cyber threats. Remember that each enhancement you make reduces your organisation’s vulnerability and demonstrates a proactive commitment to cyber security best practices.
Stage 4: Test your systems with internal vulnerability scans
Conducting thorough internal vulnerability scans is a pivotal step in preparing for your Cyber Essentials certification. These systematic assessments help you proactively identify potential security weaknesses across your organisation’s digital infrastructure before the official audit.
To perform comprehensive vulnerability scanning, you will need to use specialised automated tools that can comprehensively map and analyse your network, systems, and applications. Focus on scanning all network devices, servers, workstations, and cloud services for potential security gaps. Your scans should thoroughly examine configuration settings, detect outdated software versions, identify unpatched vulnerabilities, and check for potential misconfigurations that could compromise your security. Pay particular attention to examining user access controls, firewall rules, and endpoint protection mechanisms.
A critical tip is to conduct these scans regularly and not just as a one time exercise. Vulnerability management is an ongoing process that requires continuous monitoring and immediate remediation of any discovered weaknesses. By treating vulnerability scanning as a routine practice, you demonstrate to auditors your commitment to maintaining a robust and proactive security posture that adapts to evolving cyber threats.
Stage 5: Submit your self-assessment and evidence
The final stage of your Cyber Essentials journey involves carefully preparing and submitting your comprehensive self-assessment workbook. This critical document serves as the formal record of your organisation’s cyber security practices and readiness for certification.
To complete your submission effectively, ensure you have gathered all necessary information to answer the assessment questions accurately. This involves verifying details such as network boundaries, security configurations, user access rules, and security update management processes. Ensure each answer directly correlates with the specific Cyber Essentials control requirements. Pay special attention to providing clear, concise explanations where required, demonstrating your systematic approach to cyber security. Double check that all provided information is current, accurate, and provides a comprehensive snapshot of your security infrastructure.
A strategic tip is to review your submission from an assessor’s perspective. Anticipate potential questions by providing context and explanatory notes that highlight your compliant security measures. Remember that transparency and thoroughness are key. By presenting a meticulously prepared self-assessment, you demonstrate not just technical compliance, but a genuine commitment to maintaining robust cyber security practices throughout your organisation.
Stage 6: Verify compliance and prepare for future audits
Verifying your organisation’s ongoing cyber security compliance is a critical process that extends beyond the initial Cyber Essentials certification. Implementing a strategic approach to continuous compliance monitoring ensures you remain protected and ready for annual renewal.
To effectively verify compliance, establish a systematic review process that involves regular internal checks and tracking against the Cyber Essentials framework. This means scheduling regular reviews of your security infrastructure, updating documentation, and verifying that all five technical controls remain in place. Pay close attention to tracking changes in your technology environment, reviewing user access privileges, and ensuring all software and systems are maintained with the latest security updates and vulnerability fixes.
A strategic tip is to develop a proactive compliance calendar that anticipates certification renewal and tracks evolving cyber security standards. By treating compliance as an ongoing journey rather than a one time achievement, you demonstrate to both assessors and stakeholders your commitment to maintaining robust security practices. This approach not only helps you pass future audits seamlessly but also builds a resilient security culture within your organisation.
Simplify Your Cyber Essentials Journey with Freshcyber
Understanding and meeting the demanding requirements of the Cyber Essentials audit can feel overwhelming. From documenting your security controls to conducting continuous vulnerability scans, the process demands precision and ongoing commitment. Many organisations struggle with staying compliant long after the initial certification. If you find yourself juggling limited resources and the need for clear, practical support to maintain robust cyber security, Freshcyber offers solutions tailored to your exact needs.

Explore our Cyber Essentials services dedicated to guiding you through each stage of certification and beyond. With continuous Vulnerability Management built into our approach, you can avoid last-minute audit pressures and security gaps. Start your journey to stress-free, proven compliance today by visiting https://freshcyber.co.uk and discover how our expert consultancy brings peace of mind to your cyber security management.
Frequently Asked Questions
How do I start preparing for the Cyber Essentials audit?
To begin preparing for the Cyber Essentials audit, understand the core security standards set by the UK National Cyber Security Centre. Complete a self-assessment questionnaire to analyse your current security infrastructure and identify areas that need improvement.
What key areas should I focus on when implementing security controls?
Focus on the five key areas for Cyber Essentials: firewalls, secure configuration, user access management, malware protection, and patch management. Develop an action plan to systematically address any security gaps in these areas and ensure all changes are well documented.
How often should I conduct internal vulnerability scans?
Conduct internal vulnerability scans or update checks regularly, ideally monthly or weekly, to ensure you can identify and remediate high-risk vulnerabilities within the mandated 14-day window. Make it part of your ongoing security practices to ensure you remain compliant and ready for assessment.
What documents do I need to submit for the Cyber Essentials self-assessment?
Prepare to answer the self-assessment questionnaire by gathering the necessary details about your IT infrastructure. You should have access to your network diagrams, security configuration settings, and software update records to ensure your answers are accurate. Keep this information organised and available, as your Certification Body may request specific evidence, such as a network diagram or configuration screenshots, to verify your submission.
How can I ensure ongoing compliance after receiving Cyber Essentials certification?
Implement a systematic review process that includes regular internal audits and continuous vulnerability scanning. Create a compliance calendar to track reviews, ensuring your security policies and practices remain up-to-date and effective over time.
What is the importance of documentation in the Cyber Essentials audit process?
Documentation is crucial in the Cyber Essentials audit process as it provides evidence of your organisation’s security practices. Maintain clear and organised records of configurations, policies, and improvements to demonstrate your commitment to a robust cyber security strategy.
Recommended
Comments