The Essential Guide to Continuous Vulnerability Management
- Gary Sinnott

- Dec 2, 2025
- 7 min read

Over half of British businesses experienced a cybersecurity breach in the past year, putting valuable data and reputation at risk. As digital threats grow more sophisticated, relying on old approaches leaves organisations exposed. Understanding continuous vulnerability management helps companies address risks before they become costly incidents. This guide explains how a proactive and ongoing strategy can protect your assets, keep you compliant, and strengthen your business for the future.
Table of Contents
Key Takeaways
Point | Details |
Continuous Vulnerability Management | This proactive approach systematically identifies, assesses, and addresses security vulnerabilities to maintain robust cyber defence mechanisms. |
Key Elements of Effective Programme | Include regular scanning, comprehensive asset tracking, risk prioritisation, rapid remediation, and continuous monitoring to mitigate cyber threats. |
Compliance with Legal Standards | Aligning vulnerability management with compliance requirements is essential to demonstrate due diligence and optimise legal protections. |
Benefits for Organisations | Effective vulnerability management enhances cybersecurity posture, ensures compliance, and protects business reputation while managing costs efficiently. |
Defining Continuous Vulnerability Management
Continuous vulnerability management represents a proactive cybersecurity strategy designed to systematically identify, assess, and address potential security weaknesses across an organisation’s digital infrastructure. Unlike traditional point-in-time security assessments, this approach provides ongoing monitoring and remediation of technological vulnerabilities, ensuring robust cyber defence mechanisms are consistently maintained. Vulnerability scanning techniques help businesses stay ahead of emerging cyber threats.
At its core, continuous vulnerability management involves regular, comprehensive scanning of IT systems, networks, and applications to detect potential security gaps. The process includes several critical stages: asset discovery, vulnerability identification, risk prioritisation, remediation planning, and verification. By implementing a structured approach, organisations can swiftly address potential entry points for cyber attackers before they can be exploited. Vulnerability management best practices underscore the importance of maintaining a proactive security posture.
The National Cyber Security Centre highlights the strategic significance of systematic vulnerability management. By establishing a robust process to identify and assess security vulnerabilities, businesses can significantly reduce their exposure to potential cyber risks. This approach transforms vulnerability management from a reactive task into a strategic, continuous improvement process that adapts to the evolving threat landscape. Small and medium-sized enterprises particularly benefit from such comprehensive strategies, as they provide a structured framework for maintaining robust cybersecurity defences without requiring extensive internal resources.
Key elements of an effective continuous vulnerability management programme include:
Automated and regular system scanning
Comprehensive asset inventory tracking
Risk-based vulnerability prioritisation
Rapid remediation workflows
Continuous monitoring and reporting
By integrating these components, organisations can create a dynamic, responsive security environment that minimises potential cyber risks and maintains ongoing compliance with industry standards.
Types of Vulnerability Management Approaches
Vulnerability management approaches vary widely, offering organisations different strategies to identify, assess, and mitigate potential security risks. Vulnerability assessments play a crucial role in determining the most appropriate method for an organisation’s specific technological landscape. These approaches range from reactive to proactive methodologies, each designed to address cybersecurity challenges with varying levels of comprehensiveness and strategic depth.
The National Cyber Security Centre highlights three primary vulnerability management approaches: manual assessment, automated scanning, and risk-based prioritisation. Comprehensive vulnerability identification requires a nuanced understanding of each method’s strengths and limitations. Manual assessments involve human experts meticulously examining systems for potential weaknesses, providing in-depth analysis but requiring significant time and expertise. Automated scanning, conversely, utilises advanced tools to rapidly detect vulnerabilities across entire network infrastructures, offering speed and broad coverage.

Risk-based vulnerability management represents a more strategic approach, where organisations prioritise remediation efforts based on potential business impact. This method involves categorising vulnerabilities according to their severity, potential exploitation likelihood, and potential consequences. By focusing resources on the most critical vulnerabilities, businesses can efficiently allocate their cybersecurity budgets and minimise potential attack surfaces. Small and medium-sized enterprises particularly benefit from this approach, as it allows them to manage cybersecurity effectively without requiring extensive resources.
Key vulnerability management approaches include:
Manual Vulnerability Assessment
Detailed, expert-driven examination
Comprehensive but time-consuming
Automated Vulnerability Scanning
Rapid, comprehensive network analysis
Consistent and repeatable processes
Risk-Based Vulnerability Prioritisation
Strategic resource allocation
Focus on high-impact potential vulnerabilities
Continuous Monitoring
Real-time vulnerability tracking
Immediate threat detection and response
By understanding and implementing these diverse approaches, organisations can develop a robust, adaptive vulnerability management strategy that provides comprehensive protection against evolving cyber threats.
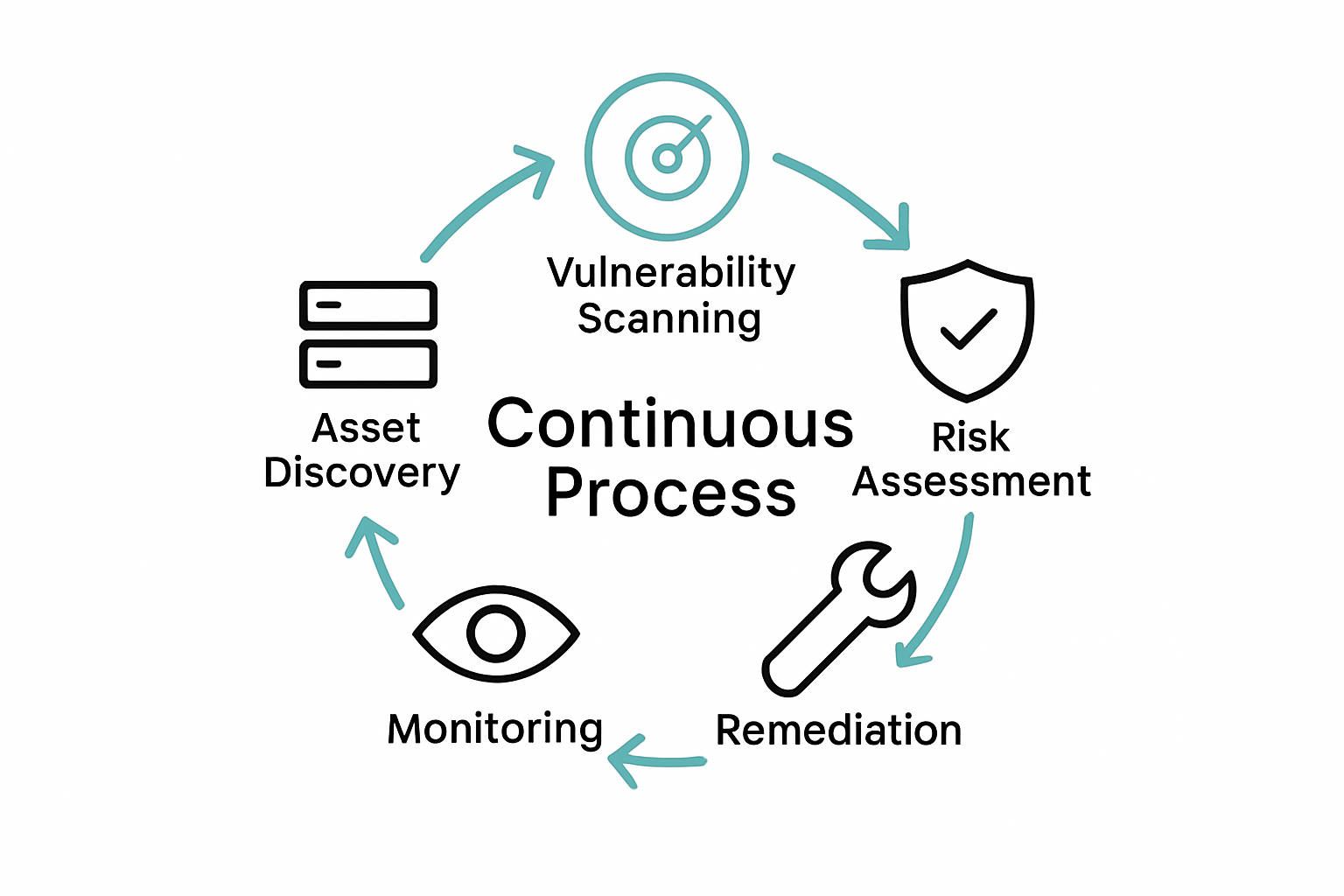
How the Continuous Process Works
Continuous vulnerability management operates through a systematic, iterative approach designed to provide comprehensive protection against evolving cyber threats. Vulnerability assessments form the foundational element of this dynamic process, enabling organisations to maintain a proactive security stance. The methodology involves multiple interconnected stages that work together to identify, evaluate, and mitigate potential security risks before they can be exploited by malicious actors.
The UK Government Security Group outlines a structured framework for implementing a comprehensive vulnerability management process. This process typically encompasses five critical stages that create a continuous improvement cycle:
Asset Discovery and Inventory
Comprehensive mapping of all digital assets
Identifying hardware, software, and network components
Creating a baseline for vulnerability tracking
Vulnerability Scanning
Automated and manual scanning techniques
Identifying potential security weaknesses
Generating detailed vulnerability reports
Risk Prioritisation
Assessing potential impact of discovered vulnerabilities
Categorising risks based on severity and exploitability
Developing targeted remediation strategies
Remediation
Implementing targeted security patches
Configuring systems to address identified vulnerabilities
Verifying effectiveness of security interventions
Continuous Monitoring
Ongoing surveillance of system security
Regular rescanning and reassessment
Tracking and documenting security improvements
By embracing this cyclical approach, organisations create a robust defence mechanism that adapts to the constantly changing cybersecurity landscape. The process ensures that security is not a one-time event but a continuous, dynamic strategy that evolves with emerging threats and technological advancements.
Compliance Requirements and Legal Standards
Navigating the complex landscape of cybersecurity compliance requires a comprehensive understanding of legal standards and regulatory requirements. Vulnerability assessments play a critical role in demonstrating an organisation’s commitment to maintaining robust security protocols and meeting stringent industry standards. Different sectors face unique compliance challenges, making it essential for businesses to develop tailored vulnerability management strategies.
The UK’s Department for Work and Pensions provides comprehensive guidance on technical vulnerability management policies, highlighting the legal frameworks that govern cybersecurity practices. Key compliance requirements typically encompass multiple regulatory standards, including:
Cyber Essentials Certification
Mandatory for many government contract bids
Demonstrates basic cybersecurity competence
Covers essential security controls
Payment Card Industry Data Security Standard (PCI DSS)
Critical for organisations processing payment transactions
Requires continuous vulnerability management
Mandates regular security assessments
General Data Protection Regulation (GDPR)
Enforces strict data protection requirements
Requires proactive security measures
Imposes significant penalties for non-compliance
Network and Information Systems (NIS) Regulations
Targets critical infrastructure and digital service providers
Mandates robust cybersecurity risk management
Requires comprehensive incident reporting
The National Cyber Security Centre emphasises that legal compliance extends beyond mere checklist completion. Organisations must demonstrate a proactive approach to identifying, managing, and mitigating security vulnerabilities. This involves maintaining detailed documentation, conducting regular risk assessments, and implementing continuous improvement processes that align with evolving legal and regulatory requirements.
By understanding and implementing these comprehensive compliance standards, businesses can protect their digital assets, build client trust, and demonstrate their commitment to robust cybersecurity practices. Effective vulnerability management is no longer just a technical requirement but a critical component of organisational governance and risk management.
Benefits for UK Businesses and Common Errors
Continuous vulnerability management offers substantial strategic advantages for UK businesses, transforming cybersecurity from a reactive cost centre into a proactive strategic asset. Common security vulnerabilities can be systematically identified and mitigated, providing organisations with a comprehensive approach to digital risk management. Small and medium-sized enterprises particularly benefit from this approach, as it allows them to develop robust security mechanisms without requiring extensive internal resources.
The National Cyber Security Centre highlights several key benefits of implementing a structured vulnerability management process. These advantages include:
Enhanced Cybersecurity Posture
Proactive threat identification
Reduced risk of successful cyber attacks
Improved organisational resilience
Compliance and Legal Protection
Meeting regulatory requirements
Demonstrating due diligence
Minimising potential legal and financial risks
Cost-Effective Risk Management
Preventing expensive security breaches
Prioritising critical vulnerabilities
Efficient resource allocation
Business Reputation Management
Building client and stakeholder confidence
Demonstrating commitment to security
Competitive advantage in tender processes
However, businesses often encounter common errors that can undermine their vulnerability management efforts. UK government security guidance identifies several critical mistakes: delayed vulnerability remediation, inadequate asset tracking, inconsistent scanning processes, and neglecting continuous monitoring. These errors can create significant security gaps, leaving organisations exposed to potential cyber threats.
By understanding both the benefits and potential pitfalls, UK businesses can develop a comprehensive vulnerability management strategy that protects their digital assets, maintains regulatory compliance, and builds long-term organisational resilience. Proactive, continuous vulnerability management is no longer a luxury but a fundamental requirement for sustainable business operations in an increasingly digital landscape.
Take Control of Your Cybersecurity with Expert Continuous Vulnerability Management
Managing vulnerabilities continuously is crucial to preventing costly security breaches and meeting essential compliance requirements like Cyber Essentials and PCI DSS. This article highlights the challenges UK businesses face in identifying, prioritising, and remediating risks effectively. If you want to stop worrying about delayed patches, inadequate asset tracking, and inconsistent scanning, it is time to adopt a proactive, structured approach to protect your organisation’s digital assets and reputation.
Freshcyber specialises in helping SMEs navigate these exact challenges through practical support tailored for busy business owners and lean IT teams. Our services not only guide you through the Cyber Essentials certification process but also offer continuous vulnerability management solutions that keep your defences strong all year round. From automated scanning and risk prioritisation to remediation and ongoing compliance, our expert team takes care of everything so your business remains resilient and audit-ready.

Start strengthening your cybersecurity today by exploring how Freshcyber’s Vulnerability Management expertise can empower your business. Visit https://freshcyber.co.uk and take the first step towards peace of mind with trusted continuous vulnerability management designed specifically for UK SMEs.
Frequently Asked Questions
What is continuous vulnerability management?
Continuous vulnerability management is a proactive cybersecurity strategy that focuses on systematically identifying, assessing, and addressing security weaknesses across an organisation’s digital infrastructure through ongoing monitoring and remediation efforts.
How does the continuous vulnerability management process work?
The continuous vulnerability management process typically involves five key stages: asset discovery and inventory, vulnerability scanning, risk prioritisation, remediation, and continuous monitoring to ensure a robust defence against evolving cyber threats.
What are the benefits of implementing a continuous vulnerability management programme?
Implementing a continuous vulnerability management programme enhances cybersecurity posture, ensures compliance with legal requirements, provides cost-effective risk management, and helps in managing business reputation by demonstrating a commitment to security.
What common mistakes should organisations avoid in vulnerability management?
Common mistakes include delayed vulnerability remediation, inadequate asset tracking, inconsistent scanning processes, and neglecting continuous monitoring, which can leave security gaps and expose organisations to cyber threats.
Recommended
Comments